If your WordPress site has been hacked, it’s important to immediately locate and close any backdoors the attacker may have left behind. A backdoor is a way for the attacker to gain unauthorized access to your site and potentially steal sensitive information or spread malware.
In this blog post, we’ll go over the steps you can take to locate and close a backdoor in a hacked WordPress site.
Our investigations found various backdoor scripts and techniques that we will discuss today.
Why do WordPress websites get hacked?
These are some significant reasons for a WordPress Website to be hacked.
- Vulnerable WordPress installation
- Outdated WP Core, themes & plugins
- Insecure hosting platform
- Weak password
- Poorly coded plugin
Let’s focus on Backdoors that may be hidden in your system if you face repeated malicious activity.
WordPress Administrator creator script
If you suspect your previous developer or an insider job, your theme & plugin is the best place to find the backdoor.
This simple script below can create a WordPress administrator account with a username as support and password: PassWord just by visiting your website this way.
example.com/?autoupdate=go
This script can hide the administrator account support from the user list and decrease the total user count by 1!
Webshell Backdoors
Web shell backdoors can be placed anywhere on your website. Most WordPress security plugins can detect only well-known web shells.
Here is some location to hide web shells on the WordPress website.
01. WordPress Themes
The majority of hidden web-shells backdoors we found into inactive themes. Because hacker knows that the site owner won’t update the theme they don’t use! The site owner’s simple thinking, the inactive theme doesn’t have anything to do with the website, so leave it!
That’s a great mistake. We recommend never to keep an unused theme installed on your website; updates or outdated don’t matter.
02. WP Plugins
Hackers choose plugins to hide backdoors because site owners are sometimes afraid to update plugins that may break the website.
Premium plugins are the main target, while pirated plugins are heaven because pirated plugins (premium plugins without a license) can’t be updated!
03. Upload Directory
The uploads directory is where all user-uploaded files, such as images; document contents, are usually stored. It’s a safe place to hide a web shell because you don’t risk being deleted by WordPress, theme, or plugin updates!
04. wp-config.php
The wp-config.php file is a popular target. Because this file contains a Database name, usernames, password, hostname, and the first file, WordPress.
05. wp-includes directory
the wp-includes directory is another place to hide the web-shell backdoor because only senior developers and security experts dare to touch this directory.
cPanel and SFTP/FTP Backdoor
Not only is your WordPress website hackable, but your web hosting control panel is an excellent place to hide the root of the hack.
01. cPanel hidden contact and a password reset email
Check these 2 files under your cPanel home directory if they contain any unknown email:
.contactmail
.contactinfo
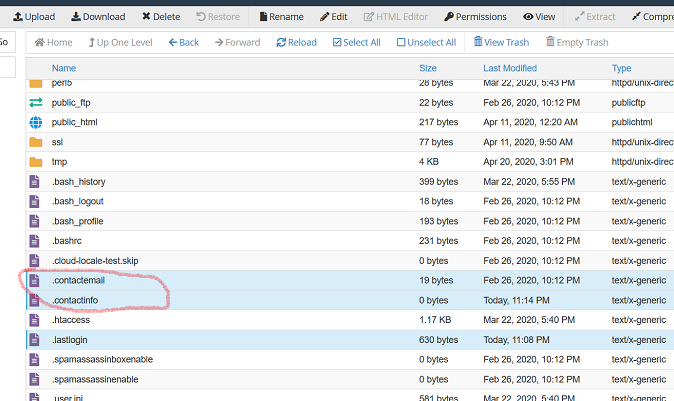
Those 2 files should contain your email address. This email address is used to send password reset emails and cPanel notifications.
Also, check .lastlogin file and see if you can recognize the IP address listed there. This is the list of IP addresses being used to access the cPanel.
Don’t forget to reset the cPanel password immediately.
02. FTP
These days FTP is not a secure protocol anymore. When doing website security hardening and trying to solve a mysterious hack coming back repeatedly, ensure you don’t have old used FTP accounts.
We recommend deleting all FTP accounts and, if possible, using SFTP with a strong password or Public Key authentication.
03. SSH key/SFTP user
Check for authorized SSH keys and SFTP user accounts in your control panel. An excellent place to hide a legit backdoor!